Espionage was a major threat to an entire nation during the cold war since any kind of information leak would lead to the enemy gaining a stronger foothold in the race for technological advancement. Although one can debate whether the cold war ever ended, we still see espionage, ransomware, and hacks as a major issue in this era we live in. Almost all developed or developing countries are connected to the World Wide Web or use the internet for transactions, deals, meetings, and so much more via desktop or mobile devices. Businesses and companies are no exception to the use of the internet and mobile devices. In this time of the pandemic, employers are forced to let their employees work from home thus increasing the use of mobile devices. Mobile devices connected to standard internet portals are subject to multiple security risks and can be a gold mine for a hacker if the device contains valuable data of an entire organization.
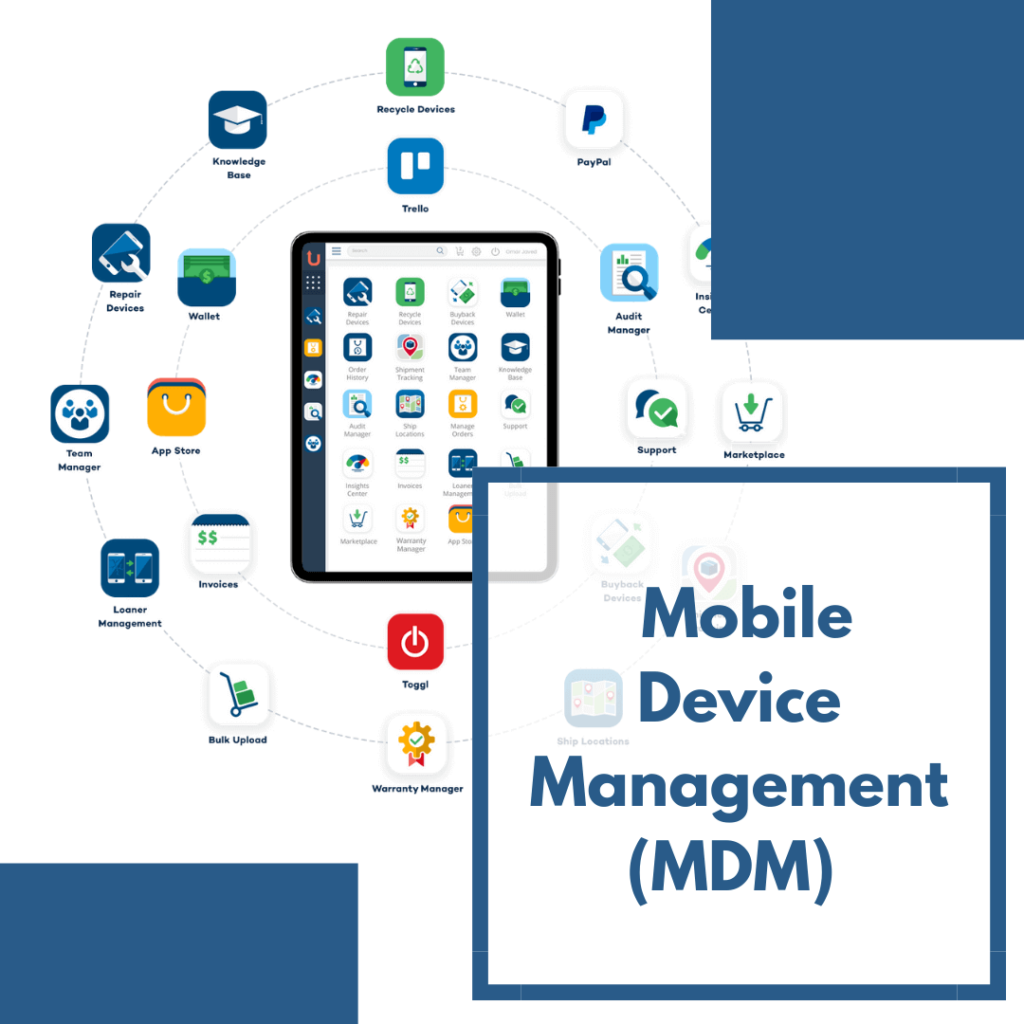
This is where Mobile Device Management (MDM) comes in to stand guard over all devices that contain the organization’s data that is marked as a liability. Unlike antiviruses and firewall protections, MDM works to centralize all devices in a single platform (server) to manage and monitor them actively and passively. This way any device which is being used to access the organization’s data servers or cloud servers can be used safely without any fear of data breach. Immunization against a virus is a top priority but fitness and a healthy lifestyle are also needed to manage prevention or recovery. This same analogy can be used for MDM. Whereas security is top on the list, the health of your device is also the priority. MDM use is like walking into a fenced multipurpose park, you have options of sports, cardio, and even calisthenics.
Unduit Wireless is one such unique fenced MDM park. A complete ecosystem of apps that helps you to manage all mobile devices on the go. To make things even better Unduit Wireless is focused mainly on the lifecycle of your devices. Offering services like repairs, buy-backs, and device refresh all the while keeping the organization’s data a top priority. Unduit Wireless presents a zero-cost repair program with these services connecting all the dots that concern the unused or damaged devices in your organization. The buy-back service provides the customer with funds gained from assets managed, which in turn can be used for other value-added services that drastically reduce the cost of services provided. Unduit Wireless even provides an enterprise calculator to estimate savings from the lifecycle MDM. Unduit Wireless unlike any other MDM is a one-stop-shop for all your solutions.